License:
Free
Operating Systems:
Windows 2003, Windows Vista, Windows Server 2008, Windows XP
Additional Requirements:
No additional requirements
Limitations:
No limitations.
Publisher's description of TrueCrypt
Protect your sensitive data with this free open-source disk encryptionsoftware. Creates a virtual encrypted disk within a file and mount itas a real disk. Encrypt an entire hard disk partition or a device, suchas USB flash drive. Automatically and transparently encrypt in realtime.
TrueCrypt provides two levels of plausible deniability, in case anadversary forces you to reveal the password: a hidden volume(steganography- more information may be found here); no TrueCryptvolume can be identified (volumes cannot be distinguished from randomdata). TrueCrypt uses encryption algorithms AES-256, Blowfish (448-bitkey), CAST5, Serpent, Triple DES, and Twofish. It is based onEncryption for the Masses (E4M) 2.02a, conceived in 1997.
Version 6.1 includes new features such as parallelizedencryption/decryption on multicore processors/systems, the ability tocreate and run an encrypted hidden operating system whose existence isimpossible to prove (Windows Vista/XP/2008/2003), and the ability toencrypt an entire system drive even if it contains extended/logicalpartitions (Windows Vista and Windows 2008).
The ultimate freeware encryption program, TrueCrypt is loaded withpowerful features that those concerned with protecting their data fromthievery should want--and have.
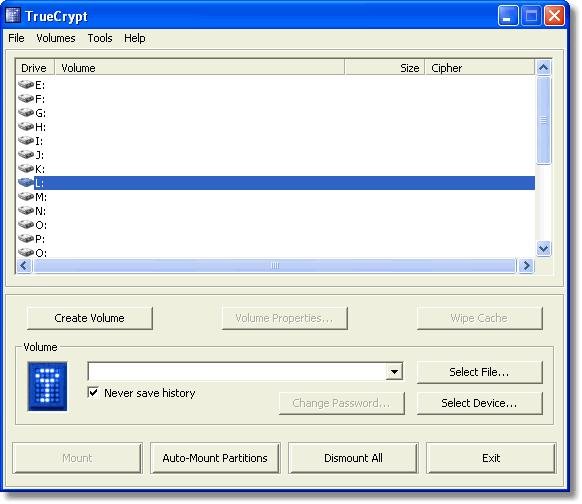
It offers 11 algorithms for encrypting your private files in apassword-protected volume. You can store your encrypted data in files(containers) or partitions (devices). TrueCrypt works hard to offerpowerful data protection, recommending complex passwords, explainingthe benefits of hidden volumes, and erasing telltale signs of theencryption process, including mouse movements and keystrokes. Thoughthe interface may not be immediately intuitive, its powerful,on-the-fly encryption for no cost still earns the freeware securitytool a top rating.
The useful tips in the extensive help manual and volume-creationwizard provide excellent guidance. In fact, they're required reading,as TrueCrypt lacks any considerable in-program help. For instance, thetutorial explains the entire concept beyond "hidden" volumes, but itdoesn't quite explain how to mount them. One obvious downside of anystrong encryption program is if you happen to forget your lengthy,secure password, you should consider any protected files as good asgone. However, once files are mounted to a local drive with yourpassword or key, they conveniently behave just like any normal files,allowing you to easily open, copy, delete, or other modify them anotherway. Dismount the volume, and voila--your previously accessible filesare now safely secure from prying eyes.
Users can even create a hidden operating system, encrypted awayfrom nosy busybodies, but make no mistake--TrueCrypt is not for thecasual encryption explorer. Be sure to thoroughly understand whatyou're doing with the program before you do something regrettable.



 Download Now
Download Now